Crypto
Poor MEGAN!
Oh, NO! Poor Megan! She’s just been bitten by a ZOMBIE! We can save her if we act fast, but the formula for the antidote has been scrambled somehow. Figure out how to unscramble the formula to save Megan from certain zombification. Enter the answer as flag{here-is-the-answer}.
The formula for the antidote:
j2rXjx9dkhW9eLKsnMR9cLDVjh/9dwz1QfGXm+b9=wKslL1Zpb45.
To get the plaintext version of the “antidote”, we can use a tool called Cyberchef. Once we introduce the string there, it automatically detects how the string was encoded. It turns out to be base64 but using the alphabet Megan35.
flag{Six-Parts-Honey-One-Part-Garlic}
To be Xor Not to Be
.$)/3<‘e-)<e’:e&'<e<‘e-)<5
On this challenge we are provided a XOR ciphered string. It seems to be a Single Byte XOR so we’re going to use a website to decrypt this string.
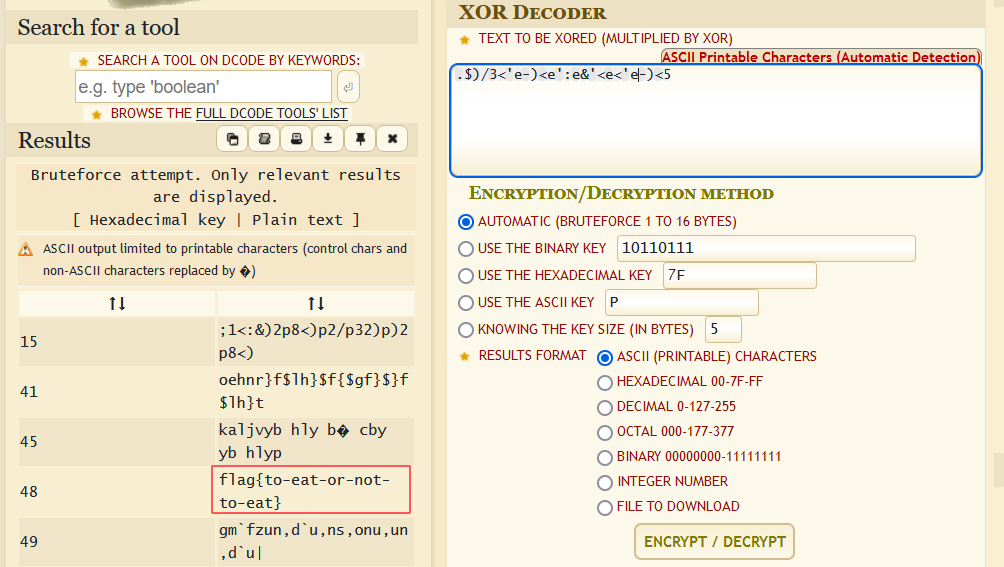
Flag:
flag{to-eat-or-not-to-eat}
Traffic Analisis
Monstrum ex Machina
Our person on the “inside” of Ghost Town was able to plant a packet sniffing device on Luciafer’s computer. Based on our initial analysis, we know that she was attempting to hack a computer in Lytton Labs, and we have some idea of what she was doing, but we need a more in-depth analysis. This is where YOU come in.
We need YOU to help us analyze the packet capture. Look for relevant data to the potential attempted hack.
To gather some information on the victim, investigate the victim’s computer activity. The “victim” was using a search engine to look up a name. Provide the name with standard capitalization: flag{Jerry Seinfeld}.
On this challenge we are given a .pcap file. We must find the name that the “victim” was searching. First we open the file in Wireshark. Since we are looking for a request on a search engine, we should focus on GET requests. Among all the requests we find this:
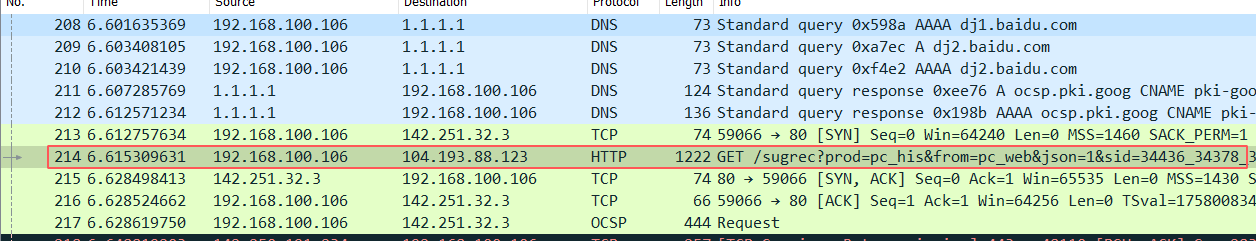
We click on ‘Follow > TCP Stream’. On the window that shows the TCP stream, we find a GET request that has the following urlencoded content:
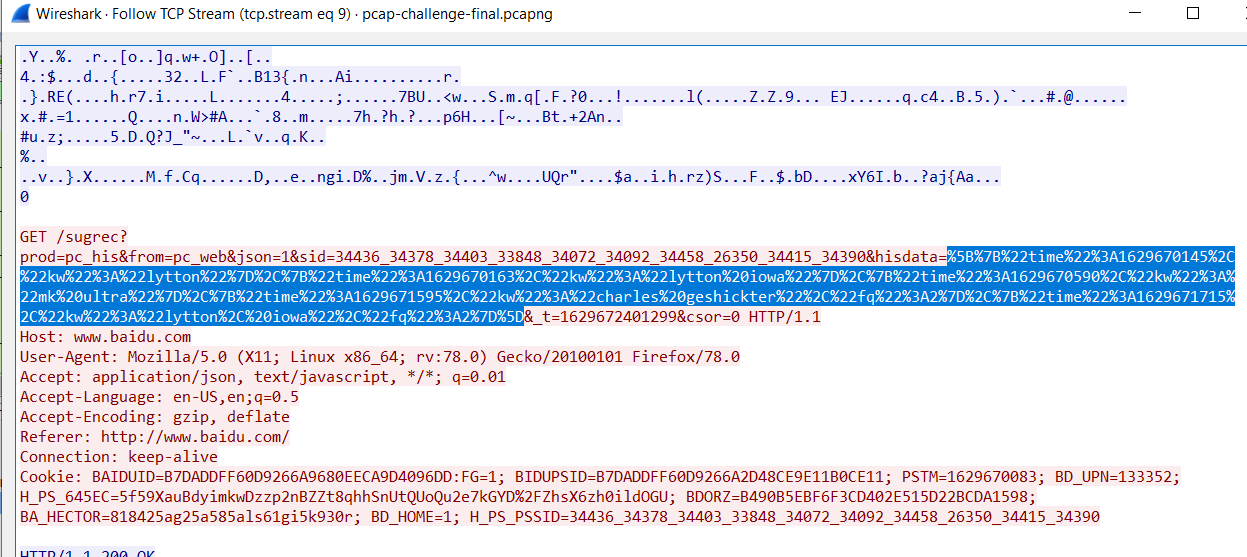
Once we decode it we have the following text.
[{"time":1629670145,"kw":"lytton"},
{"time":1629670163,"kw":"lytton iowa"},
{"time":1629670590,"kw":"mk ultra"},
{"time":1629671595,"kw":"charles geshickter","fq":2},
{"time":1629671715,"kw":"lytton, iowa","fq":2}]
And there we have the name that the “victim” was searching.
flag{Charles Geshickter}
SQL
Body count
One of our employees, Jimmie Castora, kept database backups on his computer. DEADFACE compromised his computer and leaked a portion of the database. Can you figure out how many customers are in the database? We want to get ahead of this and inform our customers of the breach.
Submit the flag as flag{#}. For example, flag{12345}.
On this challenge we are provided with a mysql database dump. Once we download it, we load it on mysql.
mysql -u user -p database < demonne.sql
Then we load mysql and execute show tables; to see the tables available in the mysql dump. Finally, to get the amount of customers on the database, we execute:
select count(*) from customers;
And we get that there are 10000 customers.
flag{10000}
Keys
One of De Monne’s database engineers is having issues rebuilding the production database. He wants to know the name of one of the foreign keys on the loans database table. Submit one foreign key name as the flag: flag{foreign-key-name} (can be ANY foreign key).
Use the MySQL database dump from Body Count.
On this challenge we need the same file than in the previous one. We only need to search for the line on the file where the table loans is defined. Once there, there are three possible flags that we can use. For example.
flag{fk_loans_cust_id}
City Lights
De Monne wants to know how many branch offices were included in the database leak. This can be found by figuring out how many unique cities the employees live in. Submit the flag as flag{#}.
Use the MySQL database dump from Body Count.
On this challenge we need to group the employees by city and the flag is the number of rows. SQL statement:
select city from employees group by city;
Flag:
flag{444}
Boom
DEADFACE actors will be targeting customers they consider low-hanging fruit. Check out Ghost Town and see who they are targeting. Submit the number of target candidates as the flag: flag{#}
Use the MySQL database dump from Body Count.
On this challenge we are provided a link to a forum where some users were talking about the attack. On that forum they suggest to attack baby boomers since they are easier to target. Therefore we use the sql database dump to retrieve all customers whose date of birth is between 1946 and 1964.
There might be an easier way to get that date range on the customers table, but I got tired of getting errors while trying to turn the dob string to a date. This is a not very elegant solution.
select first_name from customers
where dob like '%195%'
or dob like '%1960'
or dob like '%1961'
or dob like '%1962'
or dob like '%1963'
or dob like '%1964'
or dob like '%1946'
or dob like '%1947'
or dob like '%1948'
or dob like '%1949';
Flag:
flag{2809}
El Paso
The regional manager for the El Paso branch of De Monne Financial is afraid his customers might be targeted for further attacks. He would like you to find out the dollar value of all outstanding loan balances issued by employees who live in El Paso. Submit the flag as flag{$#,###.##}.
Use the MySQL database dump from Body Count.
On this challenge we need employees and loans tables, and filter by city name “El Paso”.
select sum(balance) from employees e join loans l on e.employee_id=l.employee_id where city='El Paso';
Flag:
flag{$877,401.00}